Your company logo is included in all content
Receive your branded resource in up to 48 hours.
Quick and easy distribution to your platforms.
Your resource, your choice!
This quiz is branded and licensed for your company to use however you see fit, following our standard license*.
Check out some ideas on how to use your branded cybersecurity quizzes:
Share it internally with members of your organization through internal communications channels like social media, intranet, etc.
Use this resource in your emails to alert your teams and raise awareness to the latest threats in cybersecurity.
You can print a hard copy of our posters and infographics and post throughout your building and/or campus.
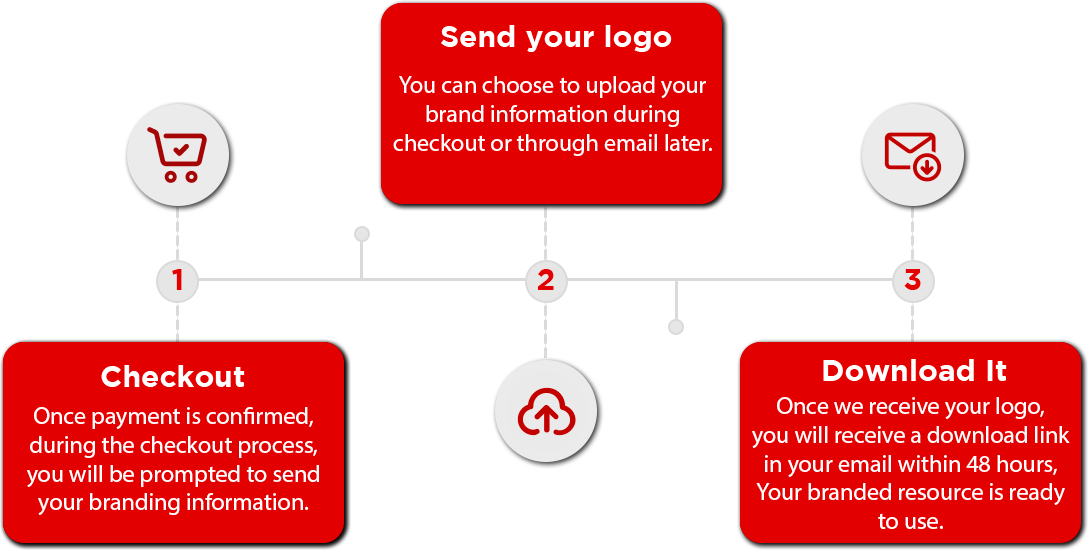
Receiving your branded resource is quick and easy.
During the checkout process, you will be prompted to upload your logo or send it via email. Once we have your brand material, we will deliver this resource branded for your organization in up to 48 hours. It will arrive via the e-mail you provided.
$500.00
A concise, 2-minute 28-second training tool that raises awareness about the growing threat of AI-powered voice and video cloning scams. It simplifies complex cyber risks into actionable tips, helping protect both your employees and their families.