$249.00

Your company logo is included in content of you purchase.
Receive your branded resource in less than 48 hours.
Content is produced with ease-of-distribution in mind.
Receiving your branded resource is quick and easy.
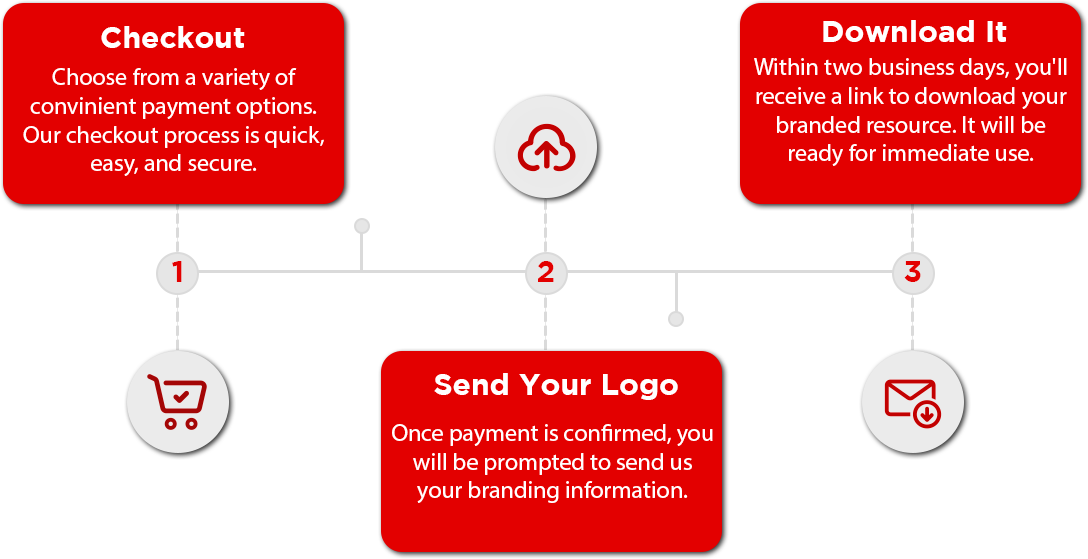
During the checkout process, you will be prompted to upload your logo or send it via email. Once we have your brand material, we will deliver this resource branded for your organization in less than 48 hours. It will arrive via the e-mail you provided.
$249.00 Original price was: $249.00.$74.70Current price is: $74.70.
Fascinating statistics about global social media usage, accompanied by simple yet memorable tips for ensuring your family’s safety when engaging with popular social platforms.
$199.00
Learn how to identify ACH fraud through business email compromise, weak passwords, incorrect “clicks” and more. Scam prevention tips and best practices are provided for your employees.
$49.00
What are chatbots and why do employees need to be aware? This 1-page reference guide is customized for your company and provides a basic user guide to chatbots including examples of different types and commands, plus safety rules.