Your company logo is included in content of you purchase.
Receive your branded resource in less than 48 hours.
Content is produced with ease-of-distribution in mind.
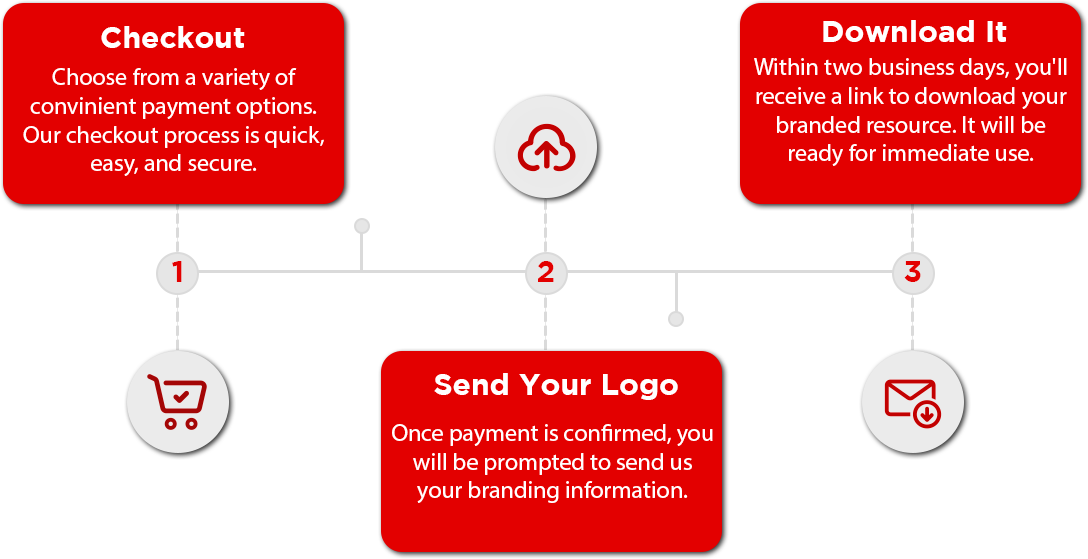
Receiving your branded resource is quick and easy.
During the checkout process, you will be prompted to upload your logo or send it via email. Once we have your brand material, we will deliver this resource branded for your organization in less than 48 hours. It will arrive via the e-mail you provided.
$49.00
This poster is one of the four in our “Who’s Hacking Me?” series, with a primary focus on phishing emails as the primary avenue threat actors employ to infiltrate organizations. Print or send online.
$49.00
A 1-page cartoon-style poster that illustrates key warning signs of business email compromise (BEC) scams and gives employees simple tips for staying vigilant.
$49.00
Employees are crazy busy before they leave for vacation. Help them get ahead of the game and stay cyber-safe when they head out.