$49.00

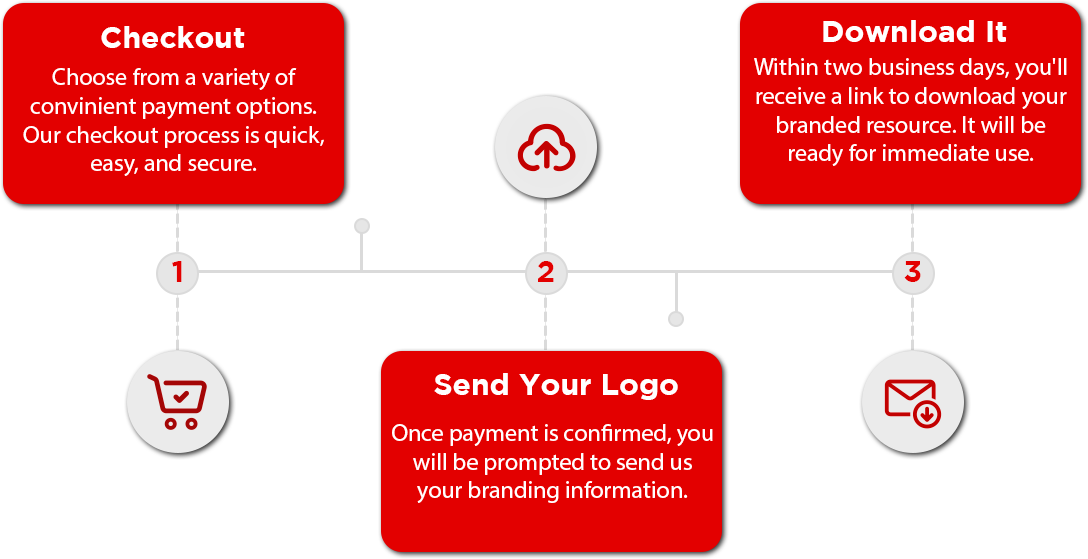
Your company logo is included in content of you purchase.
Receive your branded resource in less than 48 hours.
Content is produced with ease-of-distribution in mind.
Receiving your branded resource is quick and easy.
During the checkout process, you will be prompted to upload your logo or send it via email. Once we have your brand material, we will deliver this resource branded for your organization in less than 48 hours. It will arrive via the e-mail you provided.
$49.00
Discover 5 everyday online habits that put your security at risk—and how to fix them.
$700.00
A ready-to-deploy training kit designed to raise foundational cyber awareness among general staff and new hires.