AI-powered voice cloning is making vishing scams more convincing than ever. The Protecting Against Voice Clones infographic gives employees, students, and families a clear look at how hackers collect and use voice samples—often from social media or public recordings—to impersonate trusted individuals, commit fraud, or spread disinformation. With real-world statistics, examples of how these scams unfold, and four actionable safety tips, this colorful one-page guide is an engaging way to boost awareness and strengthen digital defenses.
$149.00

Your company logo is included in content of you purchase.
Receive your branded resource in less than 48 hours.
Content is produced with ease-of-distribution in mind.
Receiving your branded resource is quick and easy.
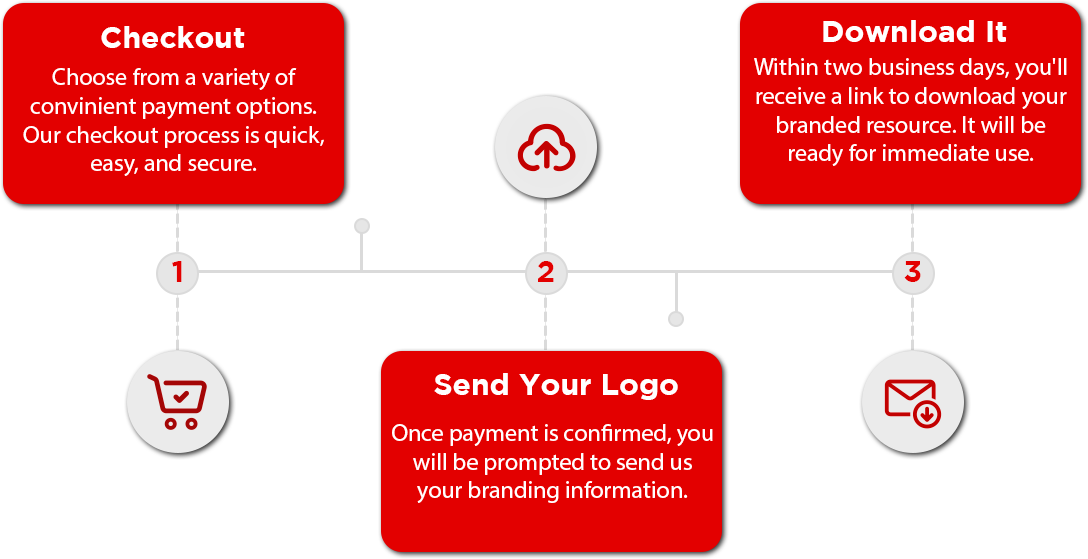
During the checkout process, you will be prompted to upload your logo or send it via email. Once we have your brand material, we will deliver this resource branded for your organization in less than 48 hours. It will arrive via the e-mail you provided.
$249.00
A short, powerful video that helps parents understand how oversharing about their kids online can lead to scams and identity theft—and what to do instead.
$49.00
As part of our “Who’s Hacking Me?” series, one of the four tailored posters underscores the concerning statistic that 20% of employees who share passwords choose to share them with their colleagues.
$49.00
Employees are crazy busy before they leave for vacation. Help them get ahead of the game and stay cyber-safe when they head out.