$49.00

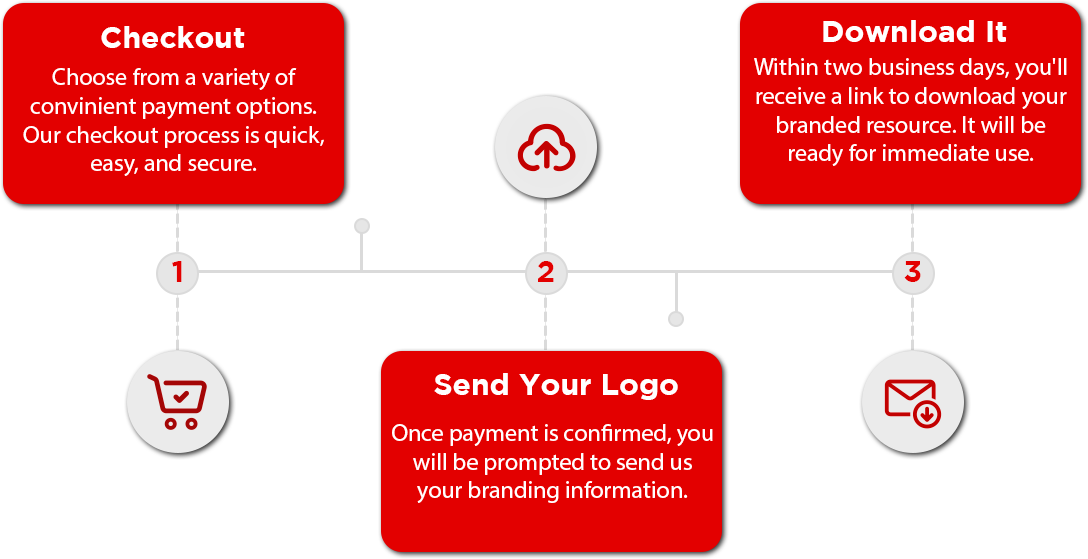
Your company logo is included in content of you purchase.
Receive your branded resource in less than 48 hours.
Content is produced with ease-of-distribution in mind.
Receiving your branded resource is quick and easy.
During the checkout process, you will be prompted to upload your logo or send it via email. Once we have your brand material, we will deliver this resource branded for your organization in less than 48 hours. It will arrive via the e-mail you provided.
$99.00
This quiz helps define some of the most common and important cybersecurity terms for your employees. Clear up any confusion with this quiz. Your logo is included on the quiz.
$199.00
Explore this live-scoring five-question quiz, focusing on the topic of smishing, designed to teach you how to distinguish between safe and unsafe web addresses while providing insights into web address structures. Customized with your branding.
$49.00
Here is a concise three-page listing of the cybersecurity terms your employees need to know — but probably do not — plus important takeaways for each term. Ransomware, Skimming, Keyloggers, Cramming, Spyware, and many more. Customized for you with your logo.