
Deceptively simple and almost imperceptible: look-alike domains are designed to trick the user’s eyes by mimicking URLs of trustworthy websites. After luring the prey into a fake website, the foundation for a series of other cyber threats is established.
The domain can be used to create a phishing website or even launch attacks such as Business Email Compromise (BEC) or ransomware with a small likelihood of being flagged by email security software. Since these domains are legitimately registered and technically aren’t doing anything unsanctioned, emails coming from them will pass through any authentication.
Take a look at these two mockup pages. Can you spot what is wrong? Can you tell which one is a look-alike domain?

Homographs and look-alike domains are among cyber criminals' sneakiest forms of attacks. They are geared to trick the untrained eye.
In this example, the second domain is the correct one for our mockup bank website. The first one, however, had the Latin "a" replaced by a Cyrillic letter that looks very similar.
Could you spot the difference? Would your team be able to?
The human factor, yes! I know, we’re always coming back to it. But here’s the truth: our brains are simply not wired to read letter by letter. We see words as a whole. We look for patterns and try to anticipate the results.
Here’s a classic example, try reading this:

Easy, right?! Even though the letters themselves are shuffled, you are still absolutely capable of reading the entire paragraph as if it was written correctly.
Hackers know this, and use it against you. Remember that “Brain Games” show on National Geographic?! Well, they watched the whole thing and took notes.
This is called Typoglycemia. It suggests people can read scrambled words as long as the first and last letters are in the right place.
In April 2017, Xudong Zheng, a security enthusiast based in New York, discovered a flaw in how browsers handle international domain names.
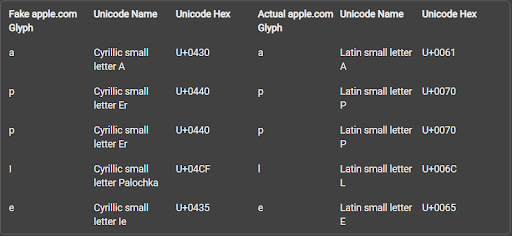
He created and registered a mock-up page for apple.com to demonstrate this flaw. However, instead of using the Latin letters we know, his domain was written in pure Cyrillic characters.
Although the domain he used looks indistinguishable from apple.com, it is a fake website that could be used to trick users into visiting it.
Zheng's page is an example of an internationalized domain name (IDN) homograph attack, where a threat actor creates and registers one or several fake domains using at least one lookalike character from a different language. Although computers read these letters differently, to the human eye, these Cyrillic glyphs can easily be confused with their Latin counterparts.
The following table shows the different hex codes assigned to them:
This particular attack can be highly successful and dangerous if used in the wild, not only undermining a company's reputation but also threatening the trust of its customers, employees, and stakeholders.
In a look-alike domain scam, the perpetrator creates a visually similar URL to that of a trusted entity. They often use common typing errors or replace characters with visually similar ones. For instance, replacing "m" with "rn" ("grnail.com" instead of "gmail.com"). These differences can be virtually unnoticeable, particularly on a mobile device or in a hastily read email.
Take a look at some examples for amazon.com :
And here are two more examples of a fictionalbank.com :
Now, let's walk through the typical steps in a look-alike domain attack.
The criminals will set up a deceptive domain, mimicking a trusted entity. The domain can be for a well-known brand, a bank, a government agency, or an internal company system.
For example, someone trying to impersonate Amazon could create the domain:

Instead of:

With the deceptive domain live, the cybercriminal sends out phishing emails or messages.
These may pose as notifications, updates, or urgent requests, designed to trick the recipient into clicking the deceptive link. Urgent and threatening messages are social tactics to heighten the chances of an unattentive user taking the bait.
Once a victim clicks on the link and provides their login credentials or other sensitive information, the fraudster can then use this data for various malicious activities, such as identity theft, financial fraud, or launching further attacks within a company network.
This might be a hard to swallow pill but the truth is: your first and strongest line of defense a company has against threats like these are its employees. Software can only go so far.
A few defensive measures to be considered to stay safe:

Look-alike domain attacks will likely remain a preferred strategy since they excel at tricking even the most vigilant among us. These threats are not simply an IT problem; they are an enterprise-wide concern, requiring active participation from everyone within the organization.
Many of these breaches are linked by a common factor: complacency.
Employees may let their guard down and become less attentive about cybersecurity when it is not a top priority in their daily tasks. The false sense of safety caused by the reliance on software solutions might be the opening cybercriminals are looking for.
Building a strong defense requires constant vigilance, education, and awareness. Reinforcing the importance of these cybersecurity issues and providing continuous training helps embed safe practices into the daily routines of employees, making them the first line of defense against such attacks.