$249.00

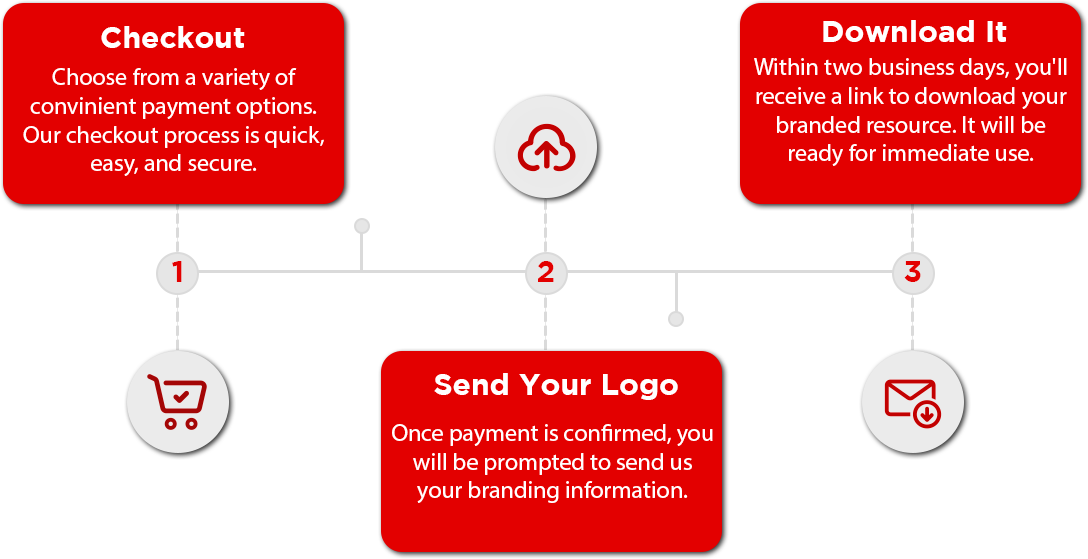
Your company logo is included in content of you purchase.
Receive your branded resource in less than 48 hours.
Content is produced with ease-of-distribution in mind.
Receiving your branded resource is quick and easy.
During the checkout process, you will be prompted to upload your logo or send it via email. Once we have your brand material, we will deliver this resource branded for your organization in less than 48 hours. It will arrive via the e-mail you provided.
$249.00
Discover five straightforward methods to enhance your online safety on personal computers – valuable knowledge for all employees. Explore browser settings, software updates, and the benefits of VPNs for a safer digital experience.
$75.00
The pandemic brought big changes to the workforce, including video conferencing from home. How can your employees best represent your company through the screen? Custom branded.
$49.00
Here is a concise three-page listing of the cybersecurity terms your employees need to know — but probably do not — plus important takeaways for each term. Ransomware, Skimming, Keyloggers, Cramming, Spyware, and many more. Customized for you with your logo.