$149.00

Your company logo is included in content of you purchase.
Receive your branded resource in less than 48 hours.
Content is produced with ease-of-distribution in mind.
Receiving your branded resource is quick and easy.
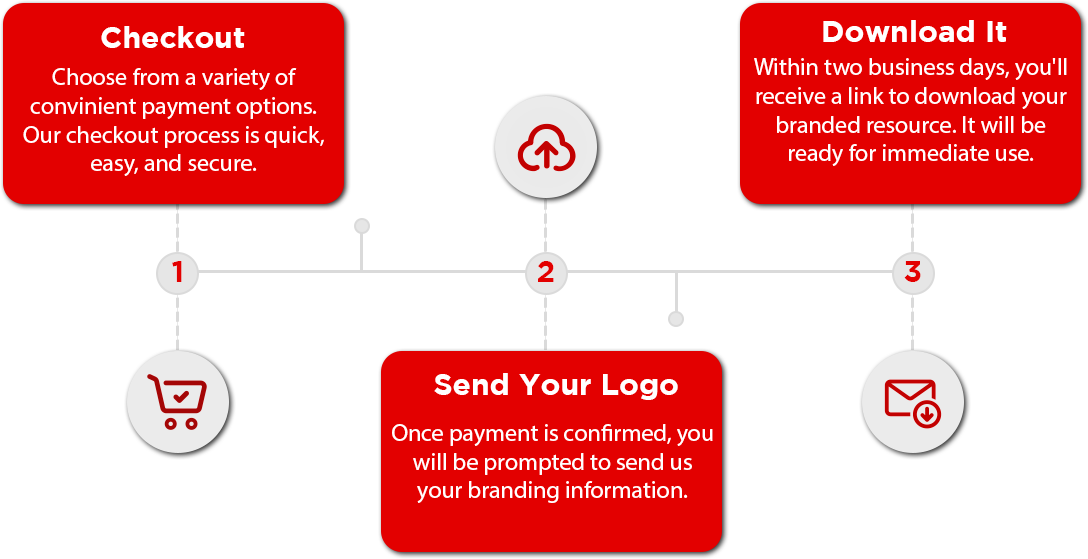
During the checkout process, you will be prompted to upload your logo or send it via email. Once we have your brand material, we will deliver this resource branded for your organization in less than 48 hours. It will arrive via the e-mail you provided.
$249.00
Here’s an easy way to remember how to spot a fake email, text, or social media post. We call it the Blood Pressure Rule. Phishing, smishing and vishing texts or emails can all raise our blood pressure due to their threatening tones and unrealistic promises. Employees learn to stop and take a breath before they “click”.
$49.00
As part of our “Who’s Hacking Me?” series, one of the four tailored posters underscores the concerning statistic that 20% of employees who share passwords choose to share them with their colleagues.
$149.00
A simple 6-step checklist to keep your data safe before deleting any app—plus the top app types most likely to compromise your privacy.